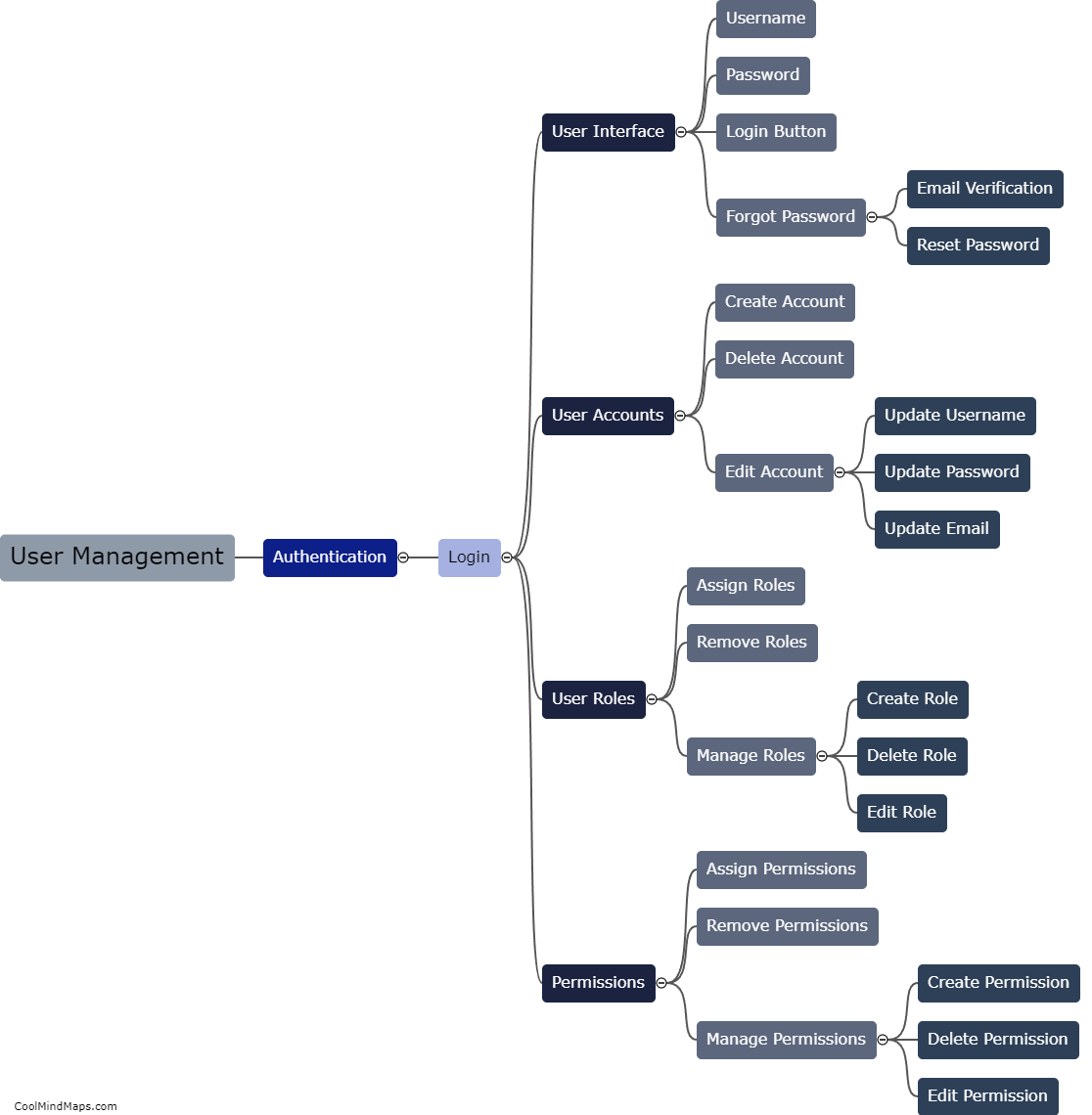
How can user management be implemented in the system?
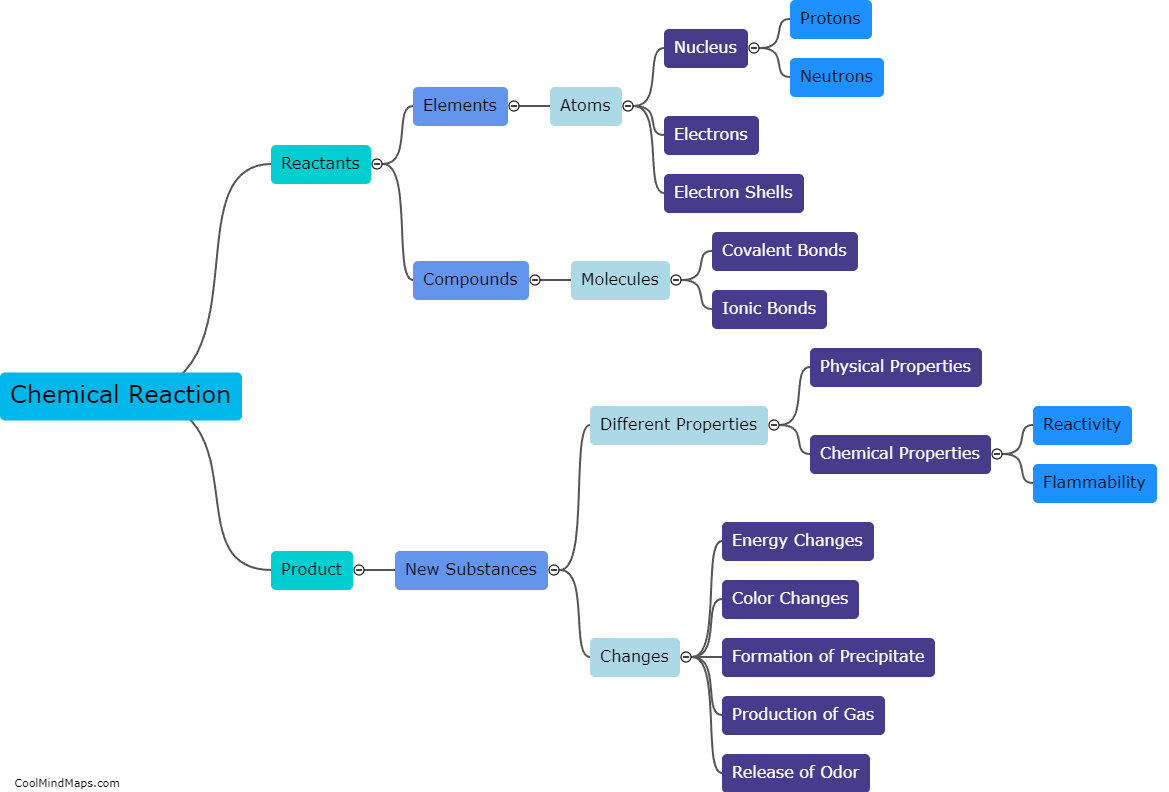
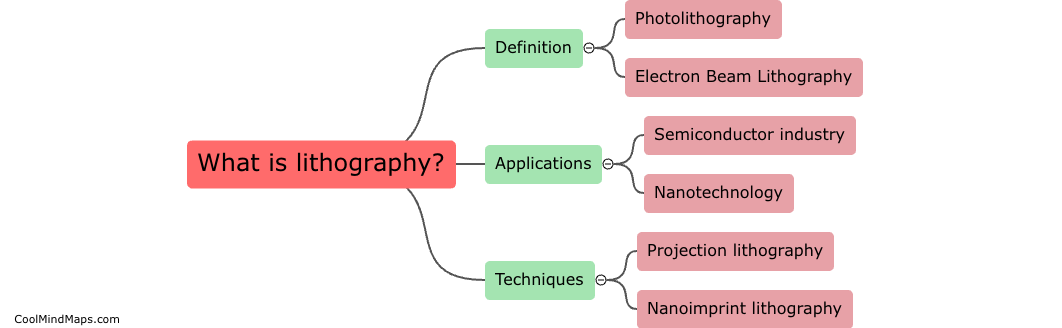
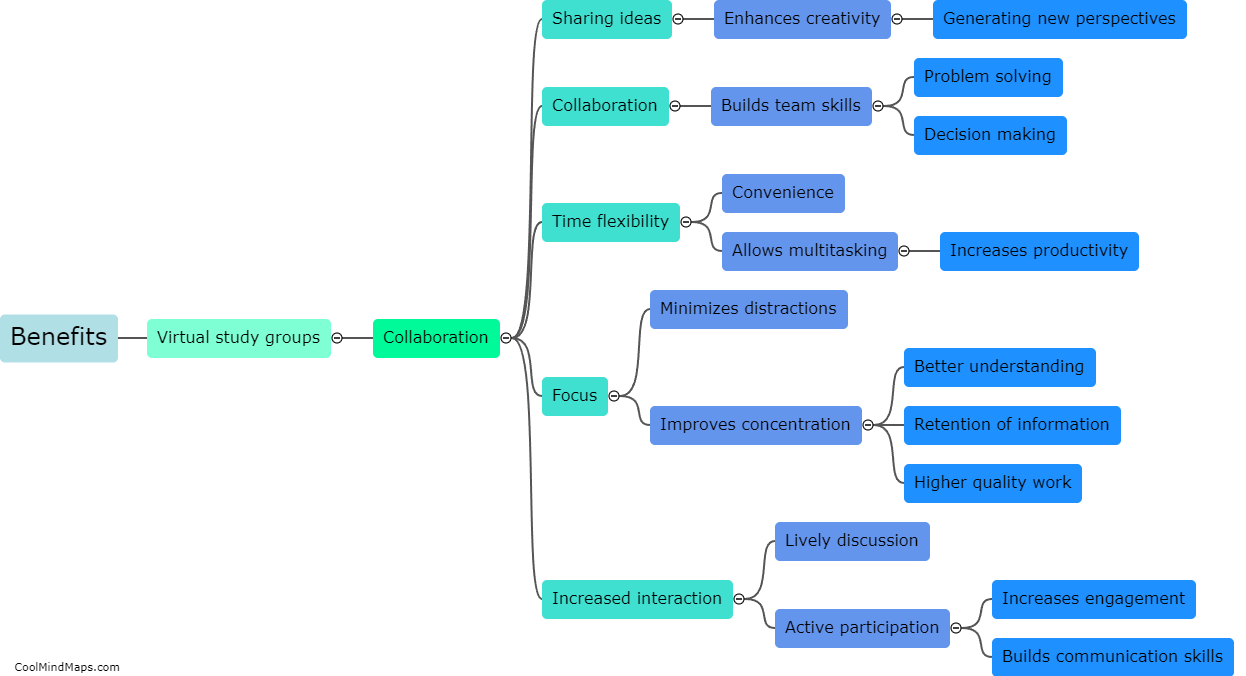
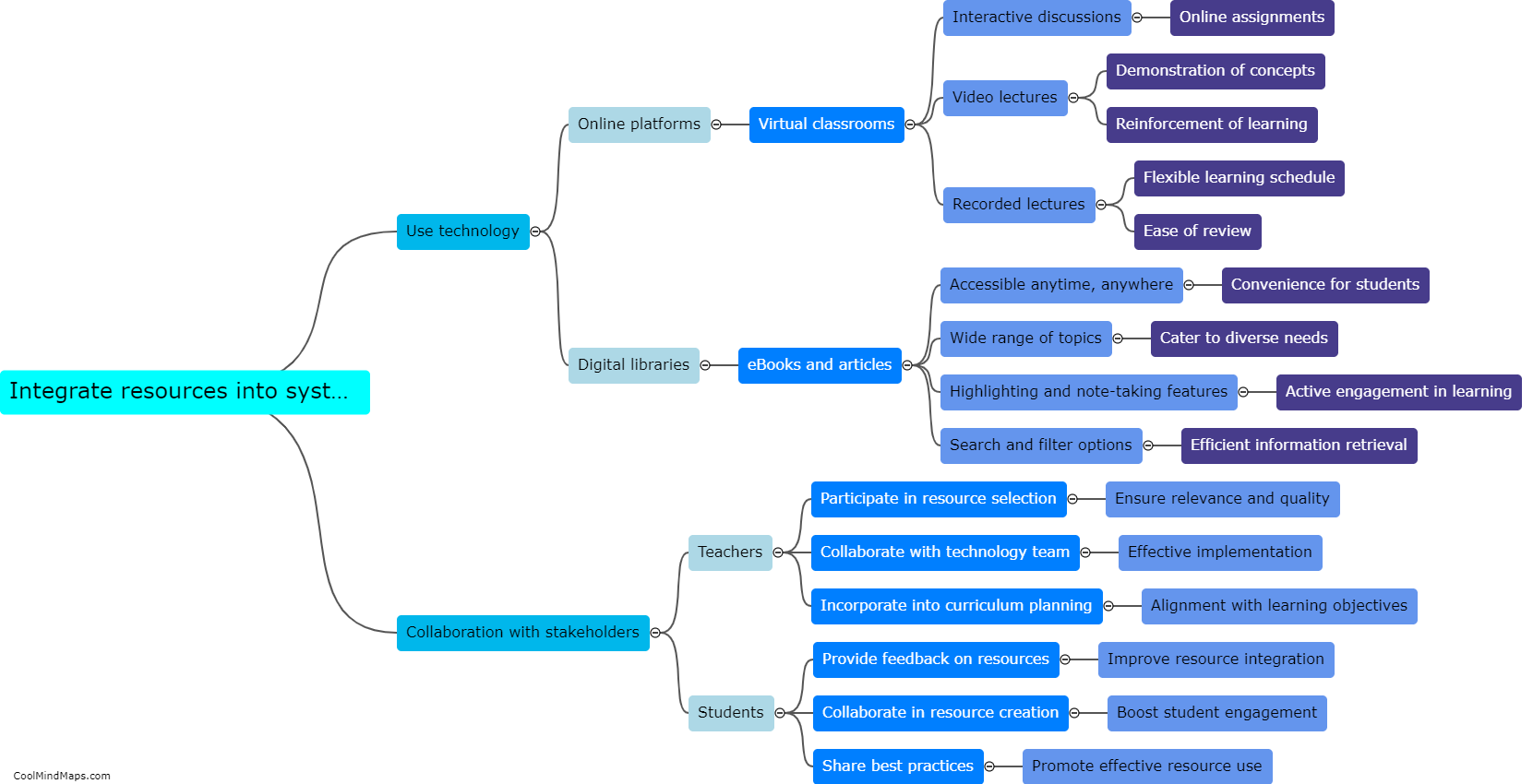
User management can be implemented in a system by following a few key steps. First, the system should provide a user registration process, where individuals can create their accounts with unique usernames and strong passwords. The next step is to incorporate authentication mechanisms, such as email verification or two-factor authentication, to ensure the identity of the users. Once registered, the system should allow for different levels of user roles, such as administrators and regular users, with corresponding permissions and access rights. Furthermore, a dashboard or user interface can be developed to allow users to manage their personal information, update passwords, and recover lost accounts. Additionally, it is crucial to implement robust security measures, like encryption, to protect user data and prevent unauthorized access. Regular audits and monitoring should also be conducted to track user activity and ensure compliance with privacy regulations. Overall, by following these steps, user management can be effectively implemented in a system, providing a secure and personalized experience for users.
This mind map was published on 20 December 2023 and has been viewed 81 times.