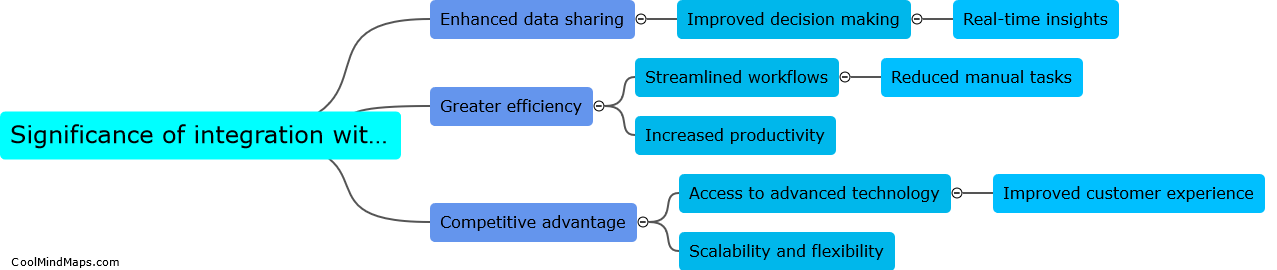
Integration with Open Blue Platform is significant as it allows businesses to streamline their operations and improve efficiency through the sharing of data and resources. By integrating with this versatile platform, companies can access a wide range of tools and services, enabling them to create...
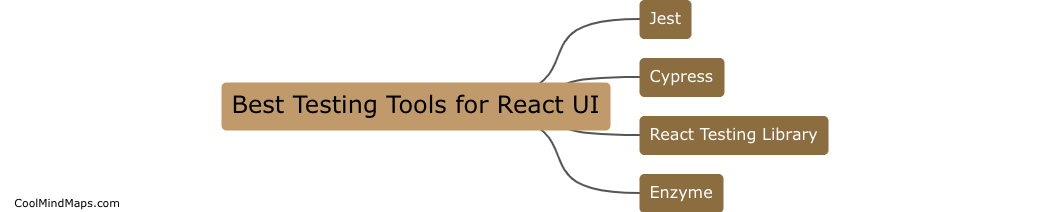
There are several testing tools available for React UI development that can help ensure your application is functioning as expected. Some of the best testing tools for React UI include Jest, Enzyme, and React Testing Library. Jest is a popular testing framework that comes pre-configured...
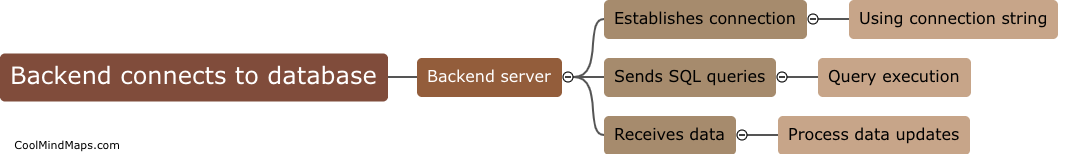
The backend connects to the database through a database management system (DBMS) that acts as an intermediary between the database and the backend application. When a user requests data from the frontend, the backend sends a query to the DBMS, which then retrieves the relevant...
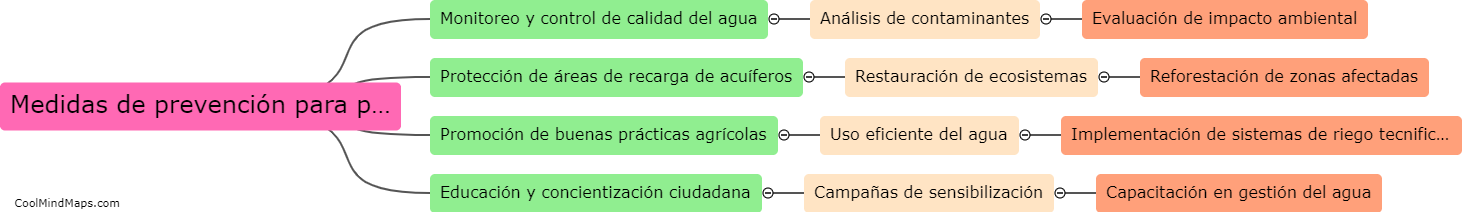
En Perú, es crucial implementar medidas de prevención para proteger las fuentes hídricas, ya que el país enfrenta desafíos relacionados con la contaminación y escasez de agua. Algunas medidas importantes incluyen promover prácticas agrícolas sostenibles que eviten el uso excesivo de agroquímicos, implementar sistemas de...
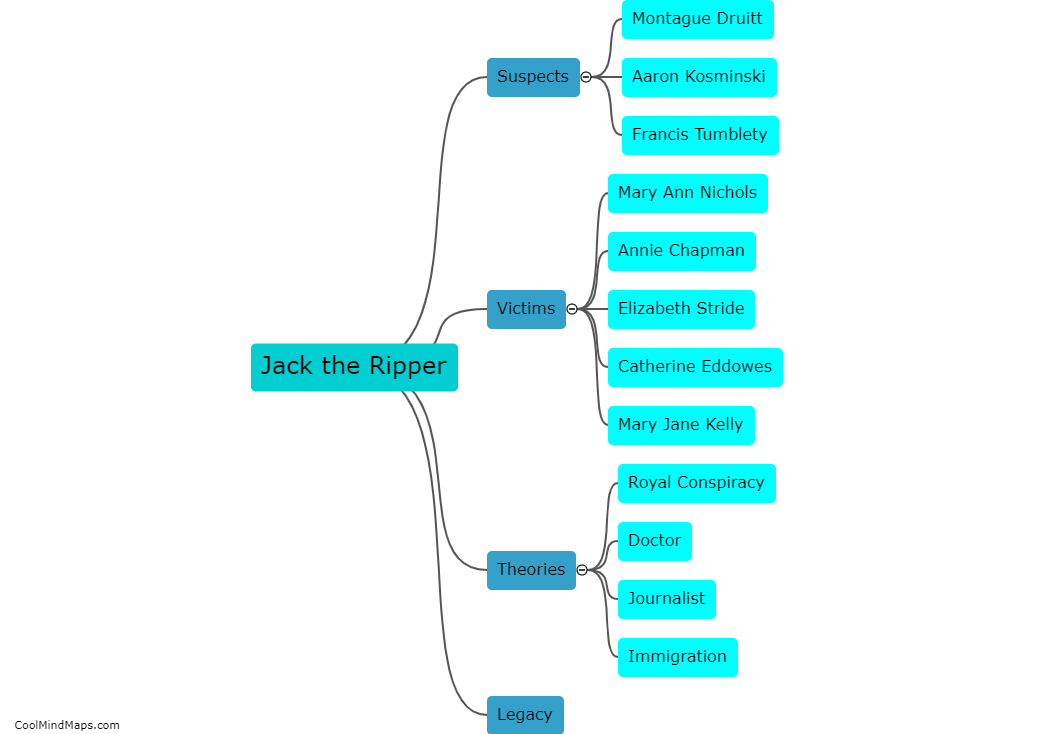
Jack the Ripper is the infamous, unidentified serial killer who terrorized the Whitechapel district of London in the late 19th century. He is believed to have committed at least five brutal murders of women, with the killings occurring between August and November of 1888. Despite...
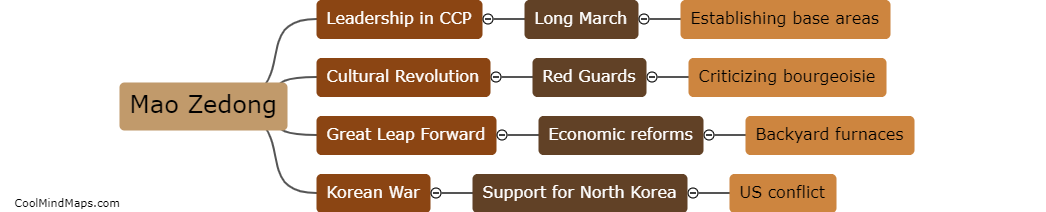
Mao Zedong was a prominent revolutionary leader and founding father of the People's Republic of China. He played a central role in the Chinese Communist Party and led the party to victory in the Chinese Civil War, establishing the People's Republic of China in 1949....

Police Station 4 is responsible for overseeing several barangays within its area of jurisdiction. Some of the barangays that fall under Police Station 4's area of responsibility include Barangay ABC, Barangay XYZ, Barangay 123, and Barangay 456. These barangays rely on the police officers of...
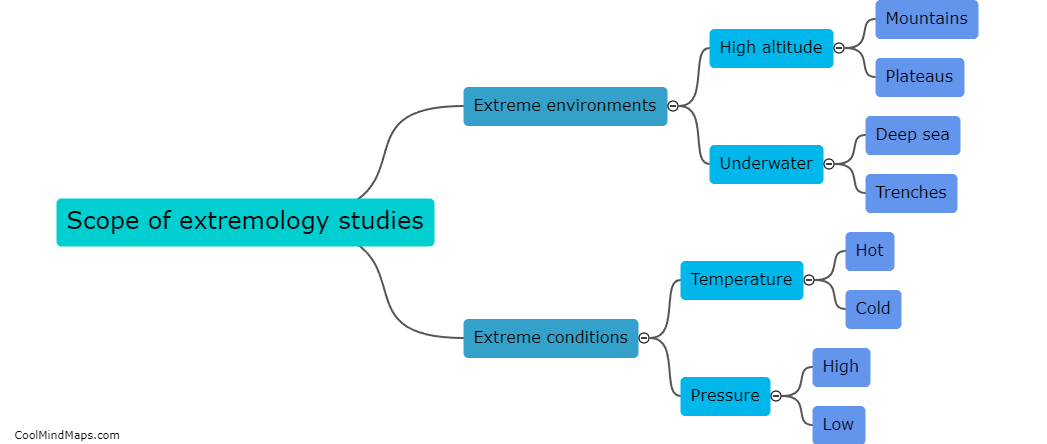
Extremology studies the physical and psychological limits that individuals can endure in extreme environments or situations. This field delves into the range of physical and mental challenges that humans can face, such as surviving in extreme climates, managing extreme stress, or pushing the boundaries of...

Nutrigenomics is the study of how individual genetic variations can affect a person's response to nutrients and diet. It explores how our genes impact how our bodies process and utilize nutrients, and how this can influence our overall health and risk of developing certain diseases....
Pour partager la joie avec les autres, il est essentiel d'être authentique et de montrer de la gratitude envers les personnes qui nous entourent. Il est important de partager les bons moments, de célébrer les réussites et de soutenir ceux qui en ont besoin. La...
La danse est intrinsèquement liée au mouvement car elle consiste en une expression artistique qui se manifeste à travers des mouvements du corps. Les danseurs utilisent leur corps pour créer une chorégraphie qui transmet des émotions et des messages au public. Le mouvement est donc...
Optical camera communication can enhance IoV (Internet of Vehicles) applications by enabling high-speed data transmission and improving the reliability of communication between vehicles and infrastructure. By using visible light communication technology, data can be transmitted through LED lights, allowing for secure and efficient communication in...
Optical camera communication in the Internet of Vehicles (IoV) offers several advantages such as high data rates, low latency, and robustness in challenging environments. This technology uses light to transmit data, allowing for rapid and efficient communication between vehicles and infrastructure. Optical camera communication also...
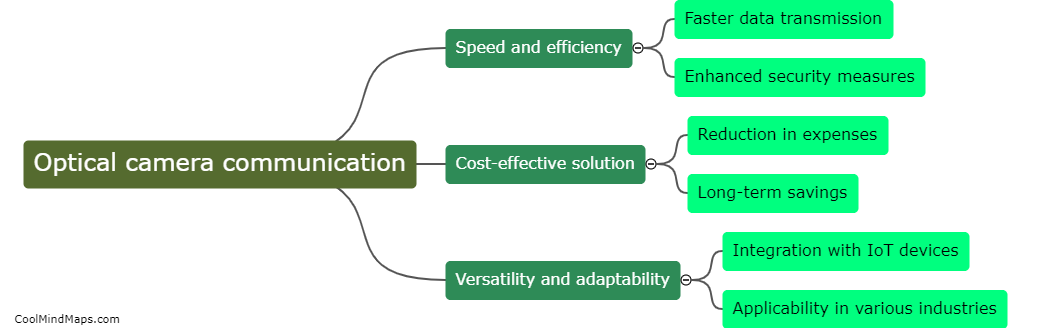
Optical camera communication, also known as Li-Fi, offers faster data transfer speeds and more secure connections compared to traditional methods such as Wi-Fi and Bluetooth. By using light waves to transmit data, Li-Fi can achieve data transfer speeds of up to 100 times faster than...
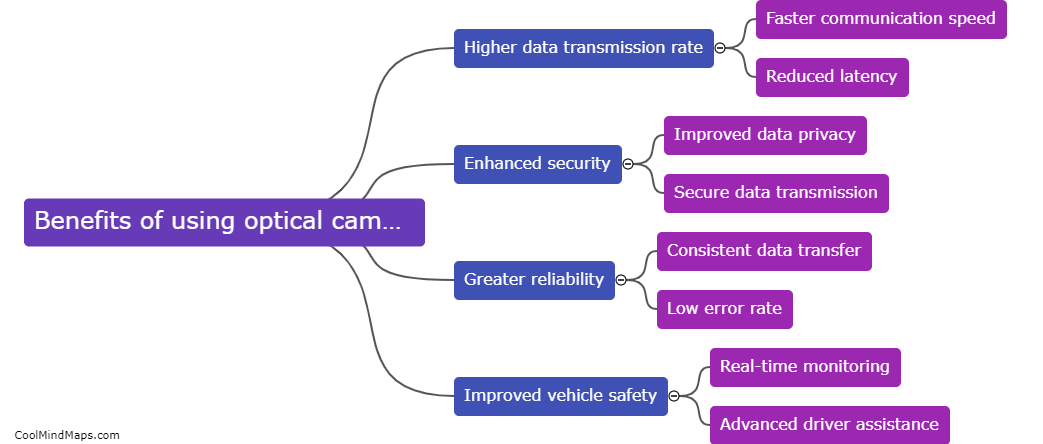
Optical Camera Communication (OCC) technology offers numerous benefits for the Internet of Vehicles (IOV) ecosystem. Firstly, OCC enables high-speed data transfer between vehicles and infrastructure without the need for additional dedicated infrastructure, reducing the burden on existing communication networks. Additionally, OCC provides enhanced security and...
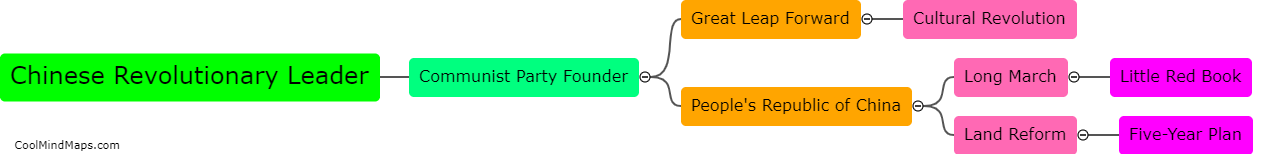
Mao Zedong, also known as Chairman Mao, is predominantly known for his role as the founding father of the People's Republic of China and as the leader of the Chinese Communist Party. He played a pivotal role in the establishment of communist rule in China...

Implementing a Change Order involves several key steps to ensure that the changes to a project are properly documented and executed. First, the change must be requested by the appropriate party, such as the client or project manager. Next, the change must be reviewed to...
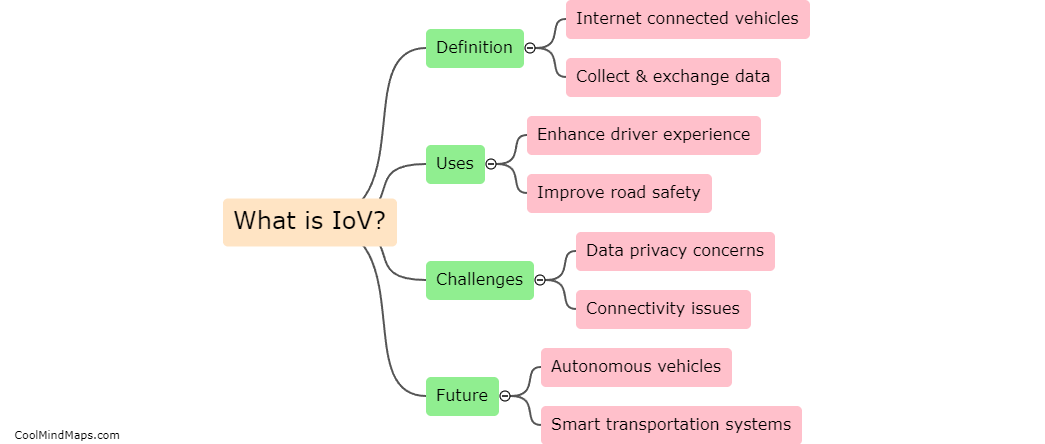
The Internet of Vehicles (IoV) refers to the network of connected vehicles that communicate with each other and with the surrounding infrastructure in order to improve safety, efficiency, and convenience on the road. IoV technology allows vehicles to share information such as traffic conditions, road...
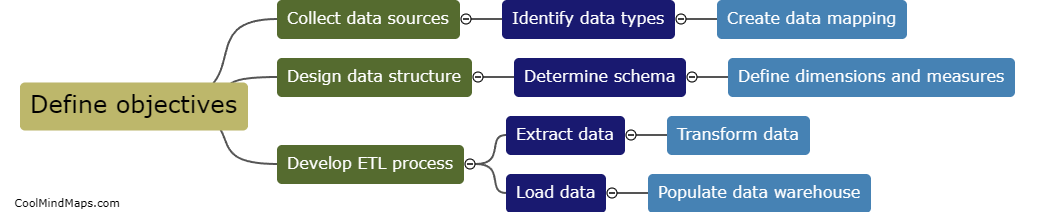
Designing a data warehouse involves identifying and understanding the business requirements, gathering data from various sources, organizing the data into a centralized repository, and creating a data model that supports reporting and analysis. It is important to consider factors such as data quality, scalability, security,...
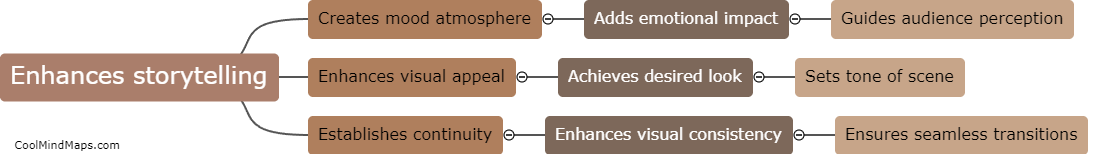
Color grading is an essential aspect of filmmaking as it can greatly enhance the mood, tone, and overall visual aesthetic of a film. By adjusting colors, contrast, and saturation, filmmakers can create a cohesive and immersive viewing experience for their audience. Color grading can also...
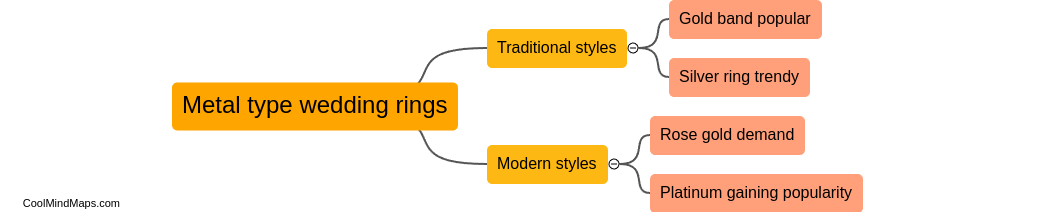
Metal type wedding rings have seen a variety of trends over the years. One of the current trends is the rise in popularity of unique and non-traditional metals for wedding rings, such as tungsten, titanium, and cobalt. These metals offer durability and a contemporary look...
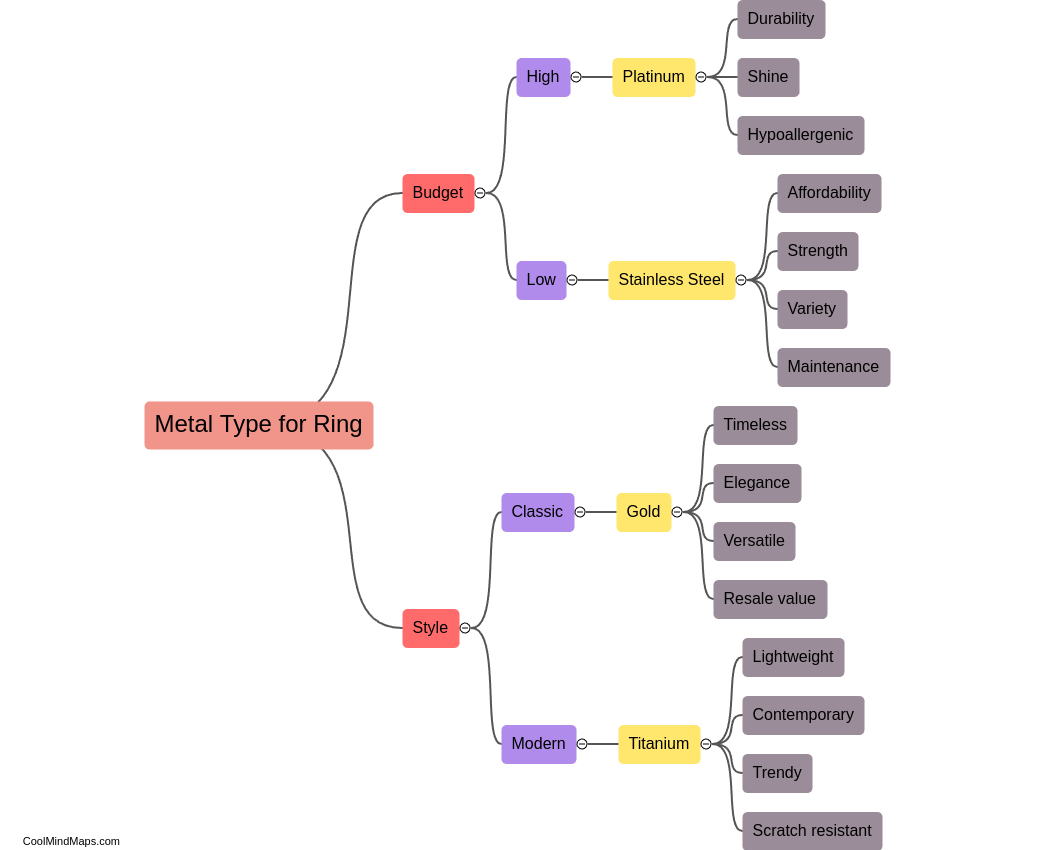
When choosing the metal type for a ring, there are several factors to consider. First, consider your skin tone and personal style. Yellow gold complements warmer skin tones, while white gold or platinum looks stunning on cooler tones. Next, think about durability and maintenance -...
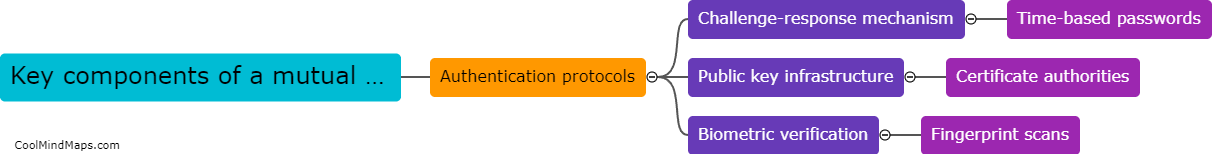
A mutual authentication scheme involves two parties, the client and the server, verifying each other's identities before establishing a secure communication channel. The key components of a mutual authentication scheme include the use of cryptographic techniques such as digital certificates, public-private key pairs, and secure...
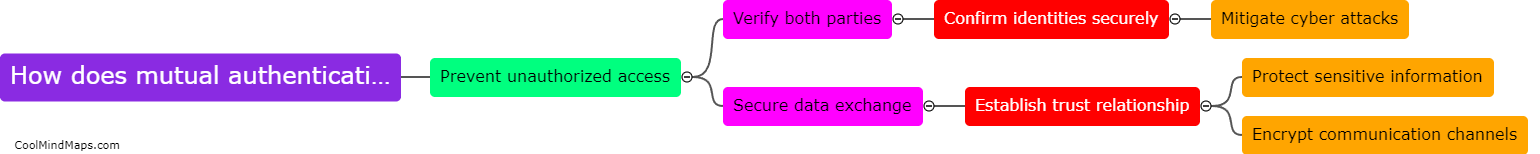
Mutual authentication plays a crucial role in enhancing security in IoT by ensuring that both the device and the network verify each other's identity before allowing communication to take place. This helps prevent unauthorized devices from gaining access to the network, as well as protecting...

Mutual authentication is crucial for industrial IoT systems because it ensures that both devices and servers verify each other's identities before establishing a connection. This helps prevent unauthorized access, data breaches, and cyber attacks, which can have serious consequences for critical infrastructure and industrial operations....

Mutual authentication in industrial IoT refers to the process of verifying the identities of both the device and the server before establishing a connection. This ensures that both parties can trust each other's identity and prevent unauthorized access to the system. By using secure protocols...
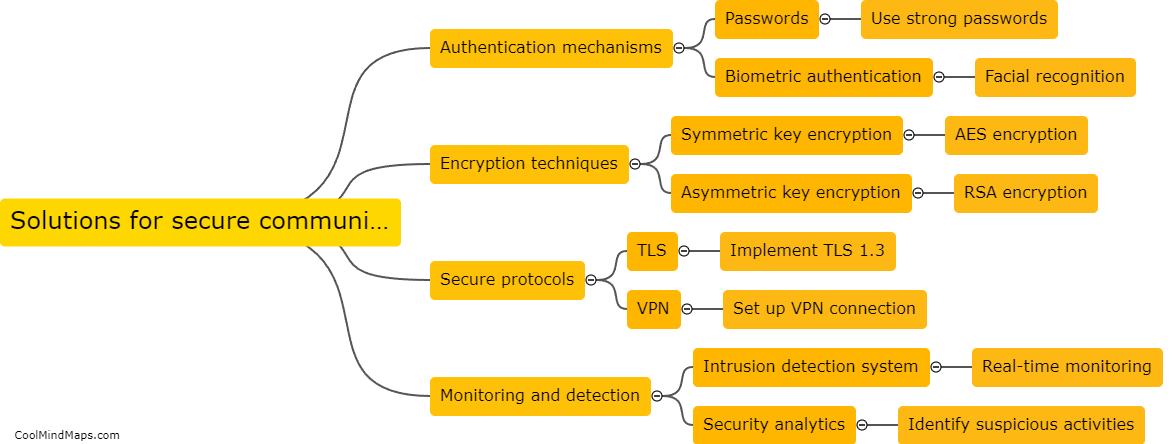
In the Industrial Internet of Things (IIoT) space, ensuring secure communication is essential to protect valuable data and prevent cyberattacks. Some solutions that can enhance security in IIoT communication include implementing strong encryption methods, using secure authentication protocols, utilizing secure sockets layer (SSL) or transport...
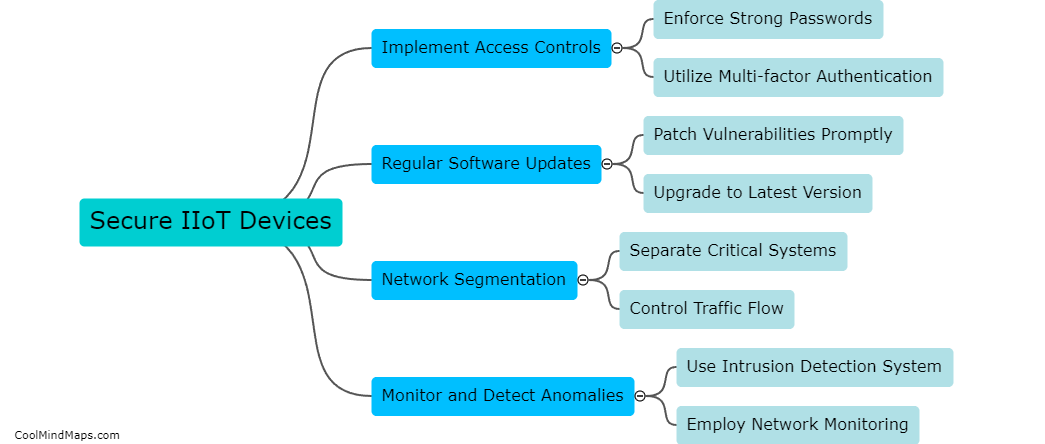
IIoT devices can be protected from cyber attacks through implementing robust security measures such as encryption, authentication, and access controls. Regular firmware updates and patches should be applied to ensure devices are running the latest security protocols. Network segmentation and firewalls can help prevent unauthorized...
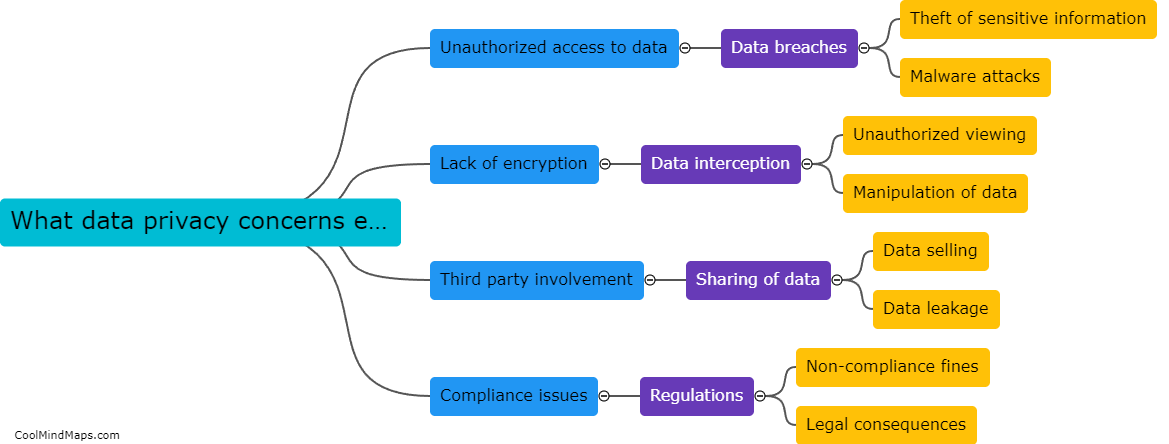
Data privacy concerns in the Industrial Internet of Things (IIoT) primarily revolve around the vast amounts of sensitive data being collected and shared between connected devices. As IIoT devices become more integrated into industrial processes and operations, the risk of unauthorized access, data breaches, and...
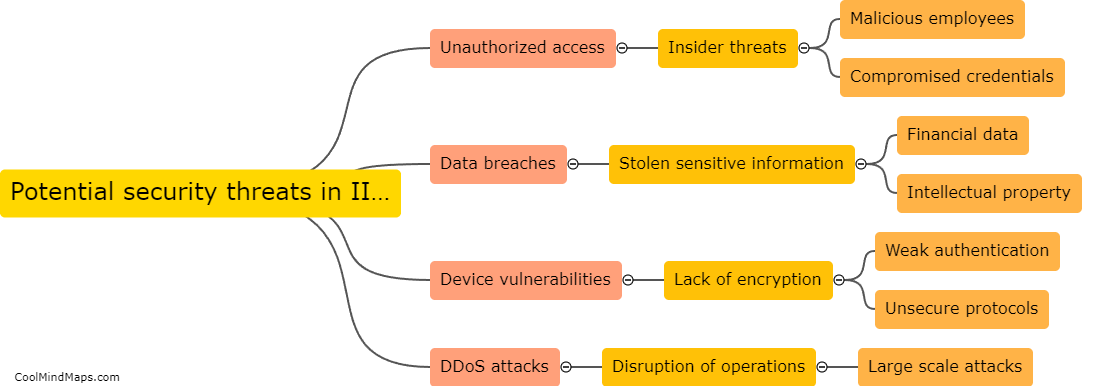
Potential security threats in Industrial Internet of Things (IIoT) include data breaches, device manipulation, and physical sabotage. Hackers can gain unauthorized access to IIoT devices and systems, allowing them to steal sensitive data or manipulate operations. Additionally, if devices are not properly secured, they can...
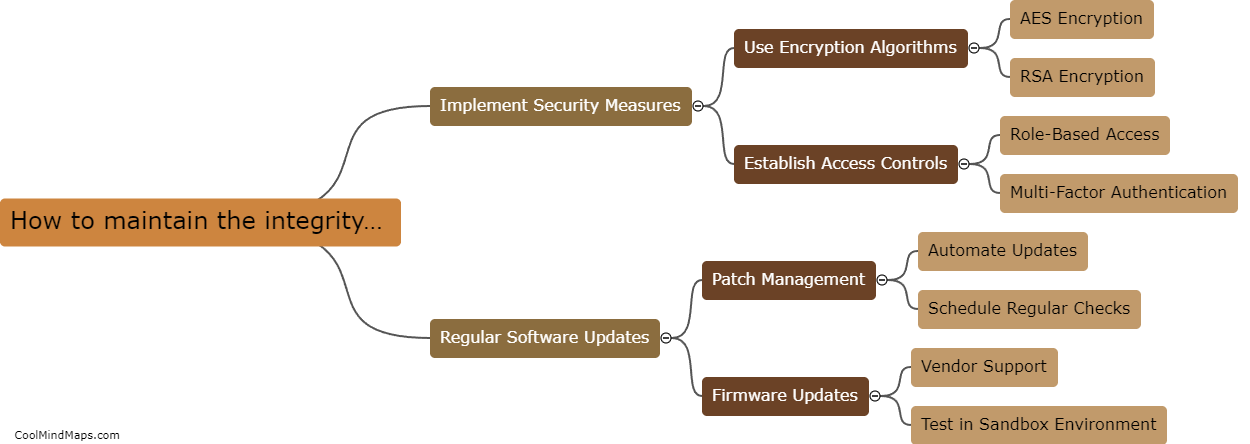
Maintaining the integrity of Industrial Internet of Things (IIoT) systems is crucial for ensuring the security and reliability of these interconnected devices. To achieve this, it is important to regularly update and patch all software and firmware, implement strong encryption protocols to protect data both...
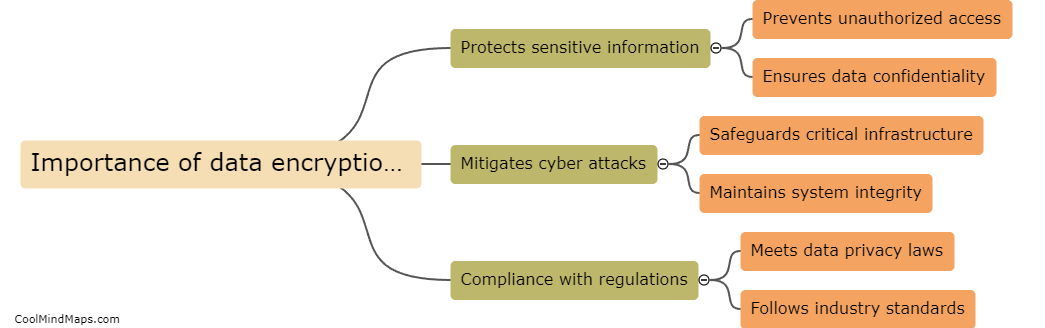
Data encryption is crucial in ensuring the security of Industrial Internet of Things (IIoT) networks. As IIoT devices collect and transmit sensitive data across networks, encrypting this data helps protect it from unauthorized access and tampering. Encryption ensures that even if data is intercepted by...
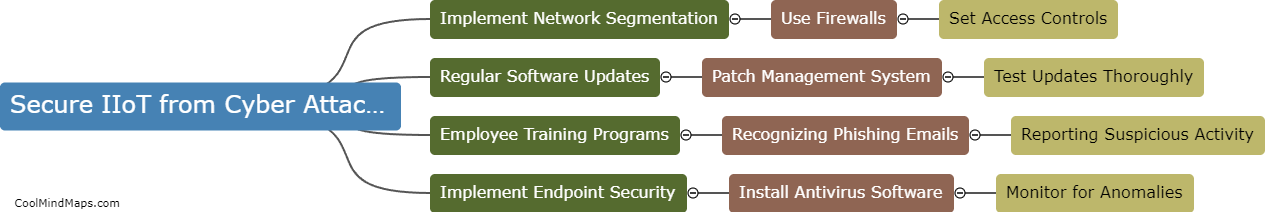
Industrial Internet of Things (IIoT) devices are often vulnerable to cyber attacks, as they are connected to the internet and may not have robust security measures in place. To secure IIoT devices from cyber attacks, it is essential to implement strong password policies, regularly update...
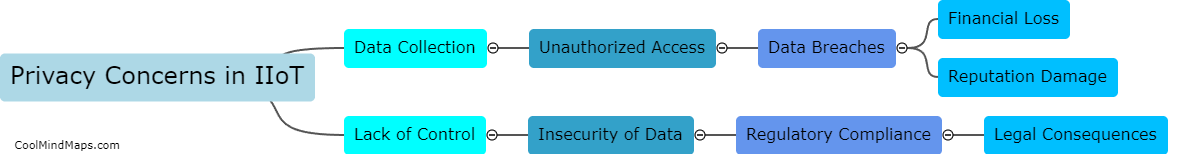
The Internet of Things (IoT) in industrial environments (IIoT) raises significant privacy concerns due to the vast amount of sensitive data that is collected and stored. This includes information related to production processes, equipment performance, and employee activities. Unauthorized access to this data could lead...

Preventing unauthorized access to IIoT data is crucial to maintaining the security and integrity of industrial systems. One way to prevent unauthorized access is by implementing strong authentication methods, such as multi-factor authentication or biometric verification. Encrypting data both in transit and at rest can...
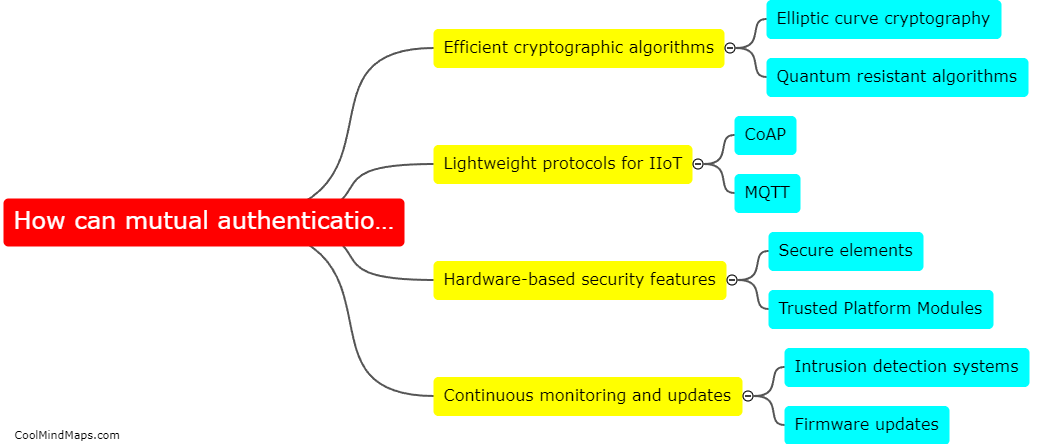
Mutual authentication schemes can be optimized for IIoT devices by implementing lightweight cryptographic algorithms, such as Elliptic Curve Cryptography (ECC), to reduce computational overhead on resource-constrained devices. Additionally, utilizing secure hardware elements, such as Trusted Platform Modules (TPMs), can enhance the security of mutual authentication...
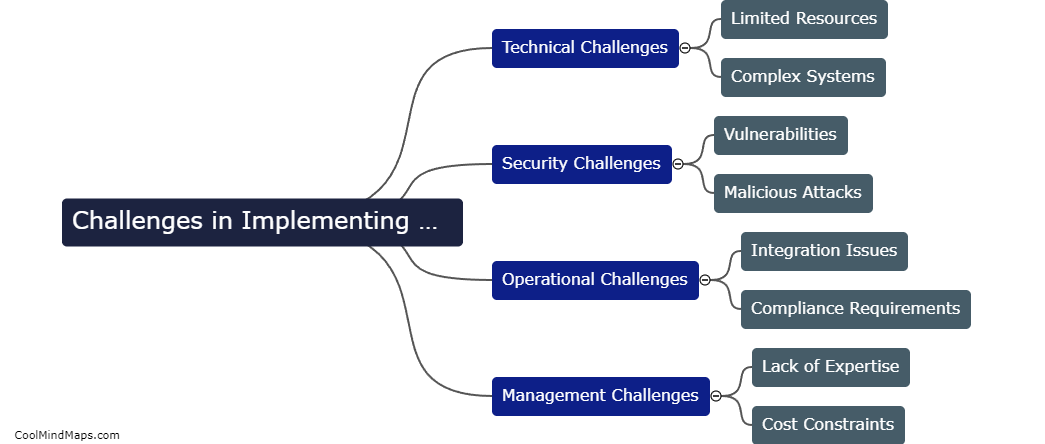
One key challenge in implementing mutual authentication in Industrial Internet of Things (IIoT) is establishing a secure and scalable identity management infrastructure. This involves securely storing and managing digital certificates, keys, and credentials for both devices and users. Another challenge is ensuring interoperability and compatibility...

Mutual authentication schemes play a crucial role in enhancing security in the Industrial Internet of Things (IIoT) by ensuring that both the devices and the network they are connecting to are verified before any communication is established. This two-way verification process helps in preventing unauthorized...
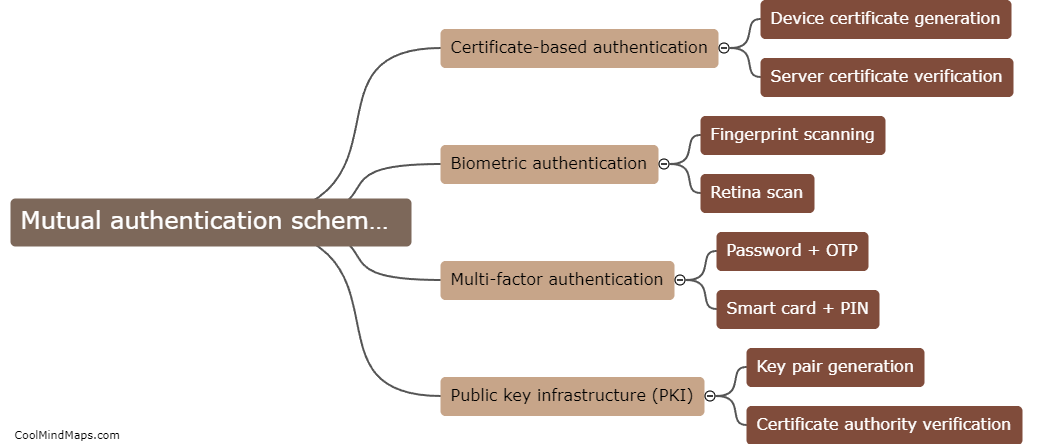
Mutual authentication schemes for Industrial Internet of Things (IIoT) involve both the device and the network verifying each other's identities before establishing a connection. This ensures that only legitimate devices can access the network and that the network can only communicate with trusted devices. Mutual...
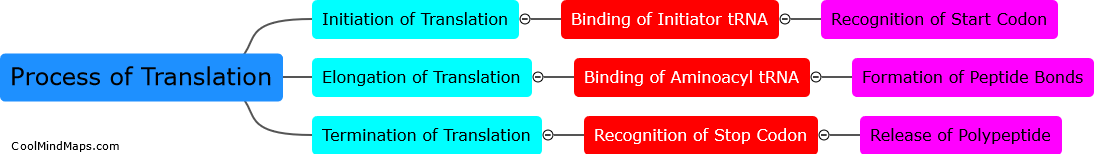
Translation is the process of conveying the meaning of text from one language to another, while maintaining the original message, tone, and style. It involves analyzing the source text, understanding its meaning, and choosing the most appropriate words and sentence structures to convey that meaning...
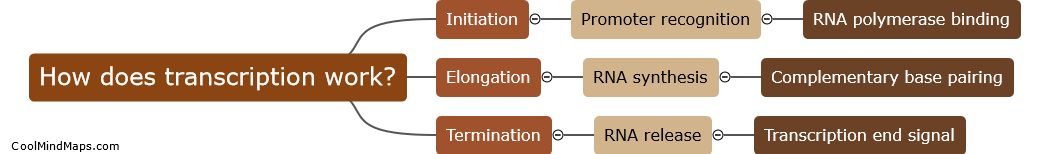
Transcription is the process in which the information encoded in a gene's DNA is converted into a complementary RNA molecule. This process is carried out by an enzyme called RNA polymerase, which reads the DNA sequence and creates a single-stranded RNA molecule that is an...
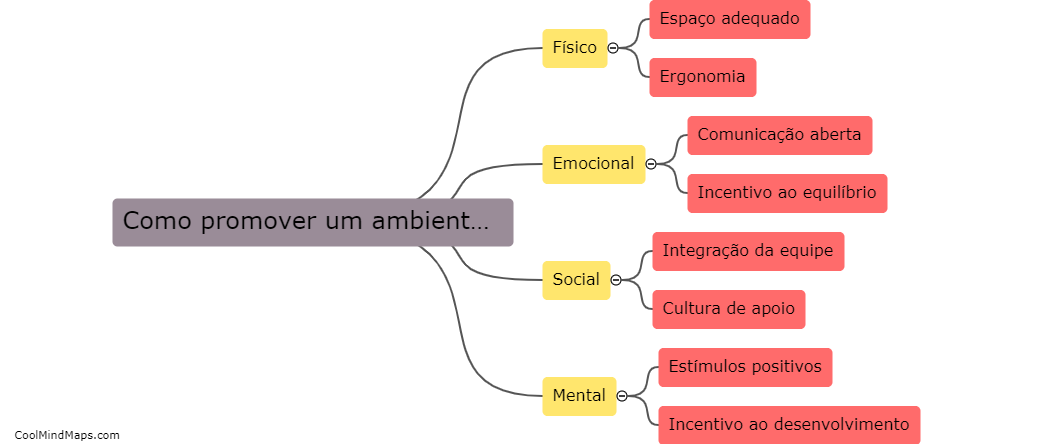
Para promover um ambiente de trabalho saudável, é essencial que haja comunicação aberta e transparente entre os colaboradores e a liderança. Investir em programas de saúde e bem-estar, como atividades físicas, sessões de relaxamento e palestras educativas, também é fundamental. Além disso, é importante incentivar...
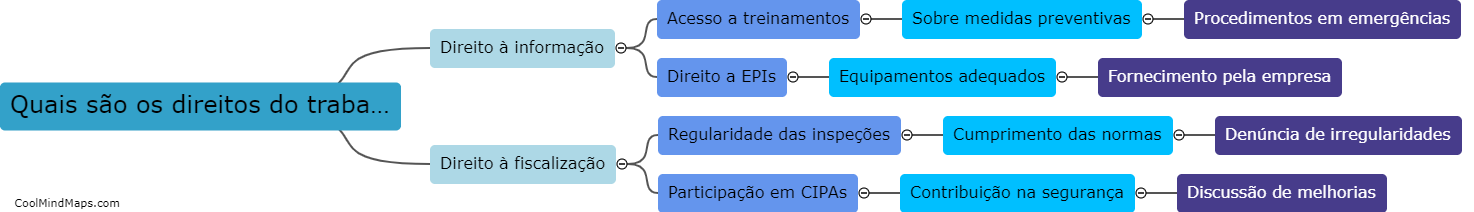
Os direitos do trabalhador em relação à segurança no ambiente de trabalho são garantidos pela legislação trabalhista e visam proteger a integridade física e mental dos trabalhadores. Estes direitos incluem condições seguras e saudáveis de trabalho, fornecimento de equipamentos de proteção individual, treinamentos sobre segurança...
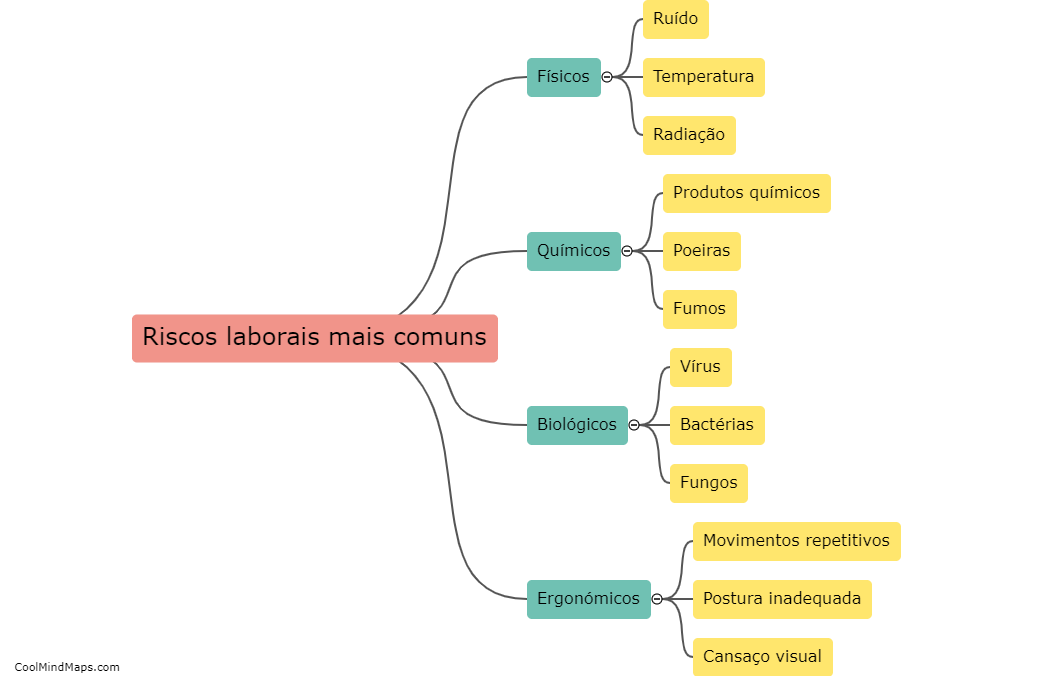
Os riscos laborais mais comuns incluem quedas, lesões musculoesqueléticas, exposição a substâncias químicas nocivas, acidentes de trânsito, estresse e assédio no local de trabalho. Estes riscos podem afetar a saúde e segurança dos trabalhadores, levando a consequências físicas, emocionais e financeiras negativas. Por isso, é...
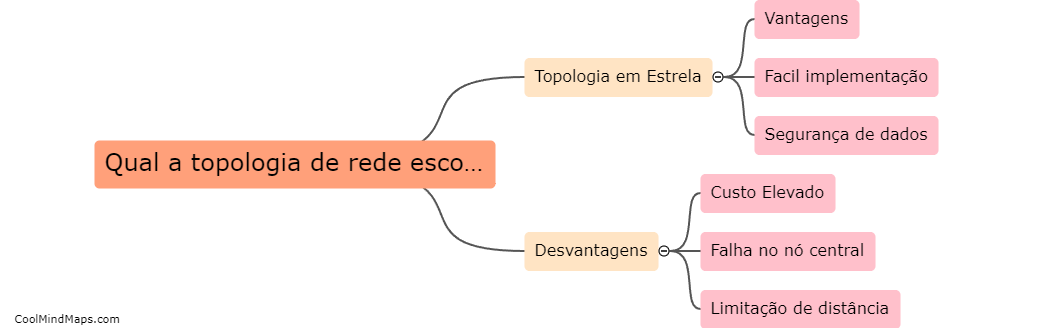
A topologia de rede escolar pode variar de acordo com as necessidades e recursos disponíveis de cada instituição de ensino. No entanto, as topologias mais comuns em ambientes escolares incluem a topologia de anel, estrela e barramento. A topologia de anel é frequentemente utilizada em...
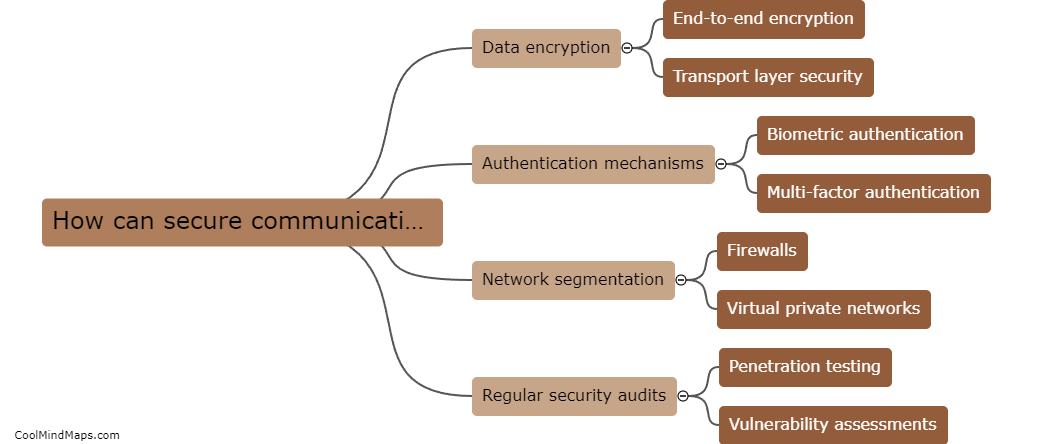
Secure communication in Industrial Internet of Things (IIoT) can be established through various methods such as using encryption techniques, implementing secure authentication protocols, using secure communication channels like VPNs, and enforcing strict access control policies. Encryption ensures that data transmitted between devices is not compromised...
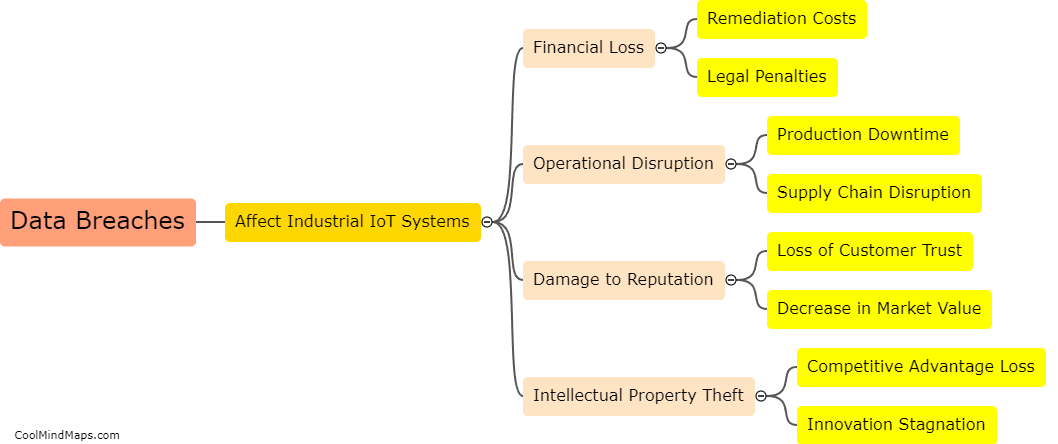
Data breaches can have severe consequences for industrial IoT systems. These breaches can compromise sensitive information, disrupt operations, and potentially damage the reputation and credibility of the organization. In the industrial sector, data breaches can result in significant financial losses, as well as potential safety...
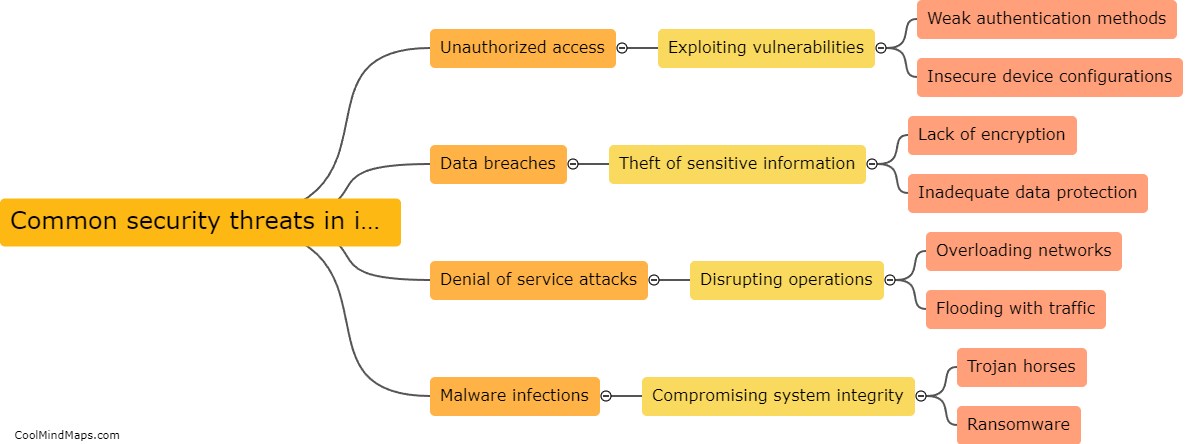
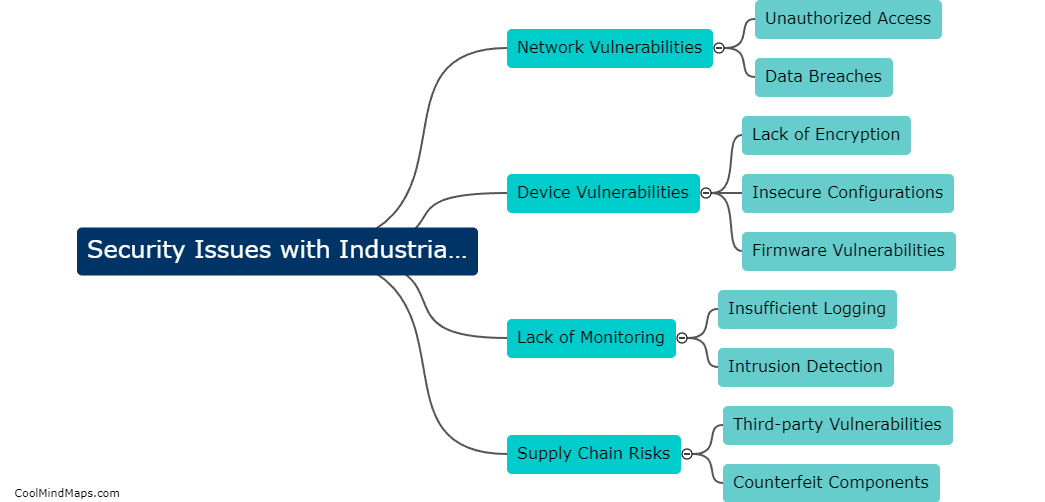
Common security threats in industrial IoT systems include unauthorized access to sensitive data or control systems, malware and ransomware attacks, denial-of-service attacks, insecure devices or sensors, lack of encryption in communication protocols, and insufficient security measures in place to protect against potential breaches. These threats...
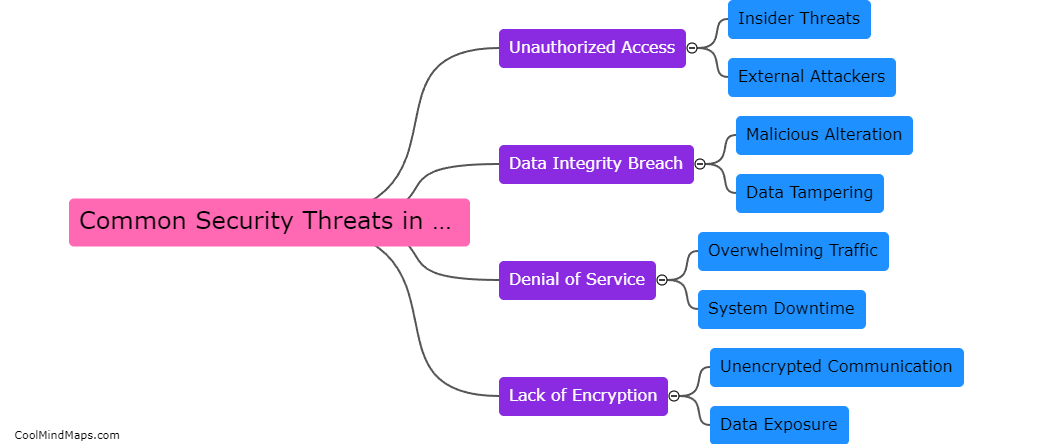
Common security threats in IIoT architecture include unauthorized access, data breaches, malware attacks, and denial of service attacks. These threats can compromise the safety of Industrial Internet of Things systems and expose sensitive data to malicious actors. It is essential for organizations to implement robust...